Planning and Implementing Network Admission Control in Your Enterprise
By
Lakshmeesha P Kadasur
—
min read



Network Admission Control (NAC) is a gatekeeper for your organization, meticulously evaluating devices before granting them network access. But implementing NAC effectively requires a well-planned strategy that aligns with your organization's unique requirements and infrastructure.
For example, a healthcare provider faces the threat of a ransomware attack due to non-compliant devices accessing the network. With a robust NAC solution in place, you can avoid such threats by ensuring that only authorized and properly configured devices gain access.
At Arche, with over 17 years of expertise in managing complex infrastructures, we understand the intricacies of deploying NAC solutions seamlessly. Our seasoned specialists have partnered with esteemed clients like Bangalore Airport, Mumbai Airport, and Sundaram Clayton, delivering innovative solutions tailored to their unique needs.
A well-defined roadmap is essential for you to implement NAC. Start by conducting a comprehensive assessment of your existing network infrastructure, identifying compatibility requirements, and defining your organization's security policies and access control objectives.
This groundwork will guide the selection and configuration of the NAC solution, ensuring seamless integration with your existing security measures, such as intrusion prevention systems (IPS), endpoint detection and response (EDR) solutions, and identity and access management (IAM) systems.
A phased rollout approach, coupled with rigorous testing and user education, can further ensure a smooth transition and maximize the benefits of your NAC investment. Continuous monitoring and timely updates are paramount, as the threat landscape is ever-evolving, and your security posture must adapt accordingly.
Are you ready to fortify your network defenses and maintain a secure, compliant environment? Book a consultation call with us today, and let's explore how our NAC expertise can become the cornerstone of your organization's comprehensive security strategy.
Deployment Strategies for NAC
How to Deploy a NAC Solution Effectively
Deploying a network admission control (NAC) solution effectively is crucial for ensuring its successful implementation and maximizing its benefits. Here's a step-by-step approach to deploying a NAC solution:
Define Policies and Requirements: Start by clearly defining your organization's security policies and requirements. Identify the types of devices that need to be monitored, the security posture criteria they must meet, and the level of access they should be granted based on their compliance status.
Conduct a Network Assessment: Perform a comprehensive assessment of your existing network infrastructure, including switches, routers, wireless access points, and other network components. This assessment will help you determine the compatibility and integration requirements for the NAC solution.
Select and Deploy the NAC Solution: Choose a NAC solution that aligns with your organization's requirements and integrates seamlessly with your existing infrastructure. Ensure that the solution supports your desired deployment model (e.g., on-premises, cloud-based, or hybrid).
Configure and Test the NAC Solution: Configure the NAC solution according to your defined policies and requirements. Thoroughly test the solution in a controlled environment to ensure proper functionality and identify any potential issues or compatibility conflicts.
Deploy NAC Agents: Install NAC agents or clients on all devices that need to connect to the network. These agents play a crucial role in assessing the security posture of devices and enforcing access control policies.
Integrate with Existing Security Solutions: Integrate the NAC solution with your existing security solutions, such as firewalls, intrusion prevention systems (IPS), and endpoint detection and response (EDR) tools. This integration ensures a cohesive security architecture and enables seamless communication and policy enforcement.
Roll Out in Phases: Rather than a big-bang deployment, consider a phased rollout approach. Start with a pilot deployment in a controlled environment or a specific department, evaluate the results, and make necessary adjustments before expanding the deployment to the entire organization.
Continuously Monitor and Update: NAC is not a one-time deployment; it requires continuous monitoring and updates. Regularly review and update your security policies, monitor the effectiveness of the NAC solution, and address any emerging threats or vulnerabilities.
User Education and Training: Educate and train your users on the importance of NAC and the procedures they need to follow to ensure compliance. Provide clear guidelines and instructions for installing and using NAC agents, as well as the consequences of non-compliance.
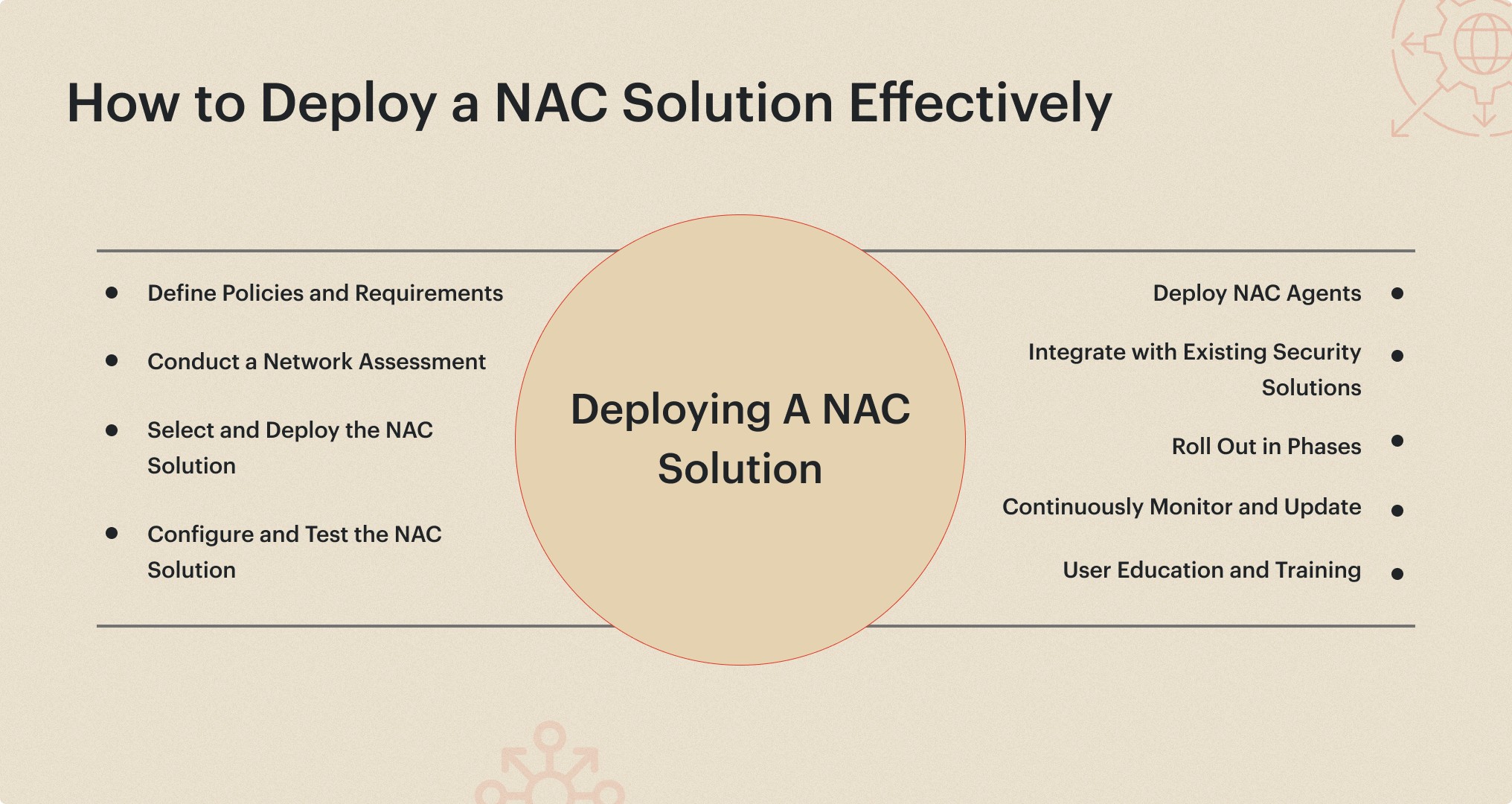
By following these steps and best practices, organizations can effectively deploy a NAC solution that enhances network security, ensures compliance, and minimizes the risk of cyber threats.
Key Considerations When Choosing a NAC Solution
Selecting the right network admission control (NAC) solution is crucial for ensuring its effectiveness and seamless integration with your existing infrastructure. Here are some key considerations to keep in mind when choosing a NAC solution:
Scalability and Performance
Evaluate the scalability and performance capabilities of the NAC solution to ensure it can handle your organization's current and future needs. Consider factors such as the number of devices, network traffic, and potential growth.
Deployment Model
Determine the deployment model that best fits your organization's requirements and infrastructure. Options include on-premises, cloud-based, or hybrid deployments. Each model has its own advantages and trade-offs in terms of control, flexibility, and cost.
Integration Capabilities
Assess the NAC solution's ability to integrate with your existing network infrastructure, including switches, routers, wireless access points, and other security solutions. Seamless integration is essential for effective policy enforcement and a cohesive security architecture.
Policy Management and Customization
Evaluate the flexibility and granularity of the NAC solution's policy management capabilities. Look for solutions that allow you to define and customize policies based on various criteria, such as user roles, device types, and security posture.
Supported Platforms and Devices
Ensure that the NAC solution supports a wide range of platforms and devices, including desktops, laptops, mobile devices, IoT devices, and various operating systems (e.g., Windows, macOS, Linux).
Remediation and Self-Healing Capabilities
Consider NAC solutions that offer automated remediation and self-healing capabilities. These features can help bring non-compliant devices back into compliance, minimizing the need for manual intervention and ensuring a more secure network environment.
Reporting and Analytics
Look for NAC solutions that provide comprehensive reporting and analytics capabilities. These features can provide valuable insights into network usage, security posture, and compliance trends, enabling data-driven decision-making and continuous improvement.

Vendor Support and Training
Evaluate the vendor's support offerings, including technical support, documentation, and training resources. Adequate support and training can help ensure a smooth deployment and ongoing maintenance of the NAC solution.
Compliance and Regulatory Requirements
If your organization operates in a regulated industry, ensure that the NAC solution complies with relevant industry standards and regulations, such as HIPAA, PCI-DSS, or GDPR.
By carefully considering these factors and aligning the NAC solution with your organization's specific requirements, you can make an informed decision and implement a solution that effectively enhances network security and ensures compliance.
If you're new to NAC and want to know everything about it, here's a blog that'll help.
Integrating NAC with Existing Network Infrastructure
NAC and Enterprise Network: Ensuring Seamless Integration
Integrating a network admission control (NAC) solution with an existing enterprise network infrastructure is a critical step in ensuring its effectiveness and maximizing its benefits. Seamless integration is essential for enabling efficient communication, policy enforcement, and a cohesive security architecture. Here are some key considerations for ensuring seamless integration:
Network Infrastructure Assessment: Conduct a thorough assessment of your existing network infrastructure, including switches, routers, wireless access points, and other network components. Identify the supported protocols, configurations, and integration requirements for the NAC solution.
Network Segmentation and VLAN Configuration: NAC solutions often leverage network segmentation and virtual local area networks (VLANs) to isolate non-compliant devices or enforce granular access controls. Ensure that your network infrastructure supports these capabilities and configure them accordingly.
Authentication and Authorization Mechanisms: Integrate the NAC solution with your existing authentication and authorization mechanisms, such as Active Directory, RADIUS servers, or other identity management solutions. This integration ensures that access control policies are enforced based on user identities and roles.
Network Access Devices Integration: Configure network access devices, such as switches and wireless access points, to communicate with the NAC solution and enforce access control decisions. This integration may involve enabling specific protocols (e.g., 802.1X, RADIUS) and configuring the appropriate settings.
Network Monitoring and Visibility: Incorporate the NAC solution into your network monitoring and visibility tools to ensure comprehensive visibility into network traffic, device connections, and potential security incidents.
Change Management and Testing: Implement a robust change management process and thoroughly test the integration between the NAC solution and your existing infrastructure. Conduct tests in a controlled environment to identify and address any potential issues or conflicts before deploying the solution in a production environment.
Documentation and Training: Document the integration process, configurations, and any necessary adjustments to existing network policies or procedures. Provide comprehensive training to network administrators and support staff to ensure they are proficient in managing and maintaining the integrated NAC solution.
By ensuring seamless integration between the NAC solution and your existing enterprise network infrastructure, you can maintain a cohesive and secure network environment, enforce access control policies consistently, and maximize the benefits of your NAC investment.
How NAC Works with Other Security Measures (IPS, EDR, etc.)
NAC is an essential component of a comprehensive security strategy, but it is most effective when integrated with other security measures, such as intrusion prevention systems (IPS), endpoint detection and response (EDR) solutions, and other security technologies.
This integration ensures a layered and cohesive security approach, enabling organizations to detect and respond to threats more effectively.
Intrusion Prevention Systems (IPS)
IPS solutions monitor network traffic and system activities for known threats and suspicious behavior. By integrating with an IPS, the NAC solution can leverage the IPS's threat intelligence and take appropriate actions based on detected threats. For example, if the IPS detects a compromised device attempting to connect to the network, it can alert the NAC solution, which can then deny or quarantine the device until the threat is mitigated.
Endpoint Detection and Response (EDR)
EDR solutions provide continuous monitoring and analysis of endpoint activities, enabling the detection and response to advanced threats and malicious behavior. When integrated with a NAC solution, the EDR can provide valuable insights into the security posture of endpoints, informing the NAC's access control decisions. For instance, if the EDR detects a non-compliant or compromised device, it can notify the NAC solution to restrict or block the device's network access.
Security Information and Event Management (SIEM)
SIEM solutions collect and analyze security-related data from various sources, enabling centralized monitoring, threat detection, and incident response. By integrating with a SIEM, the NAC solution can contribute valuable information about device connections, access attempts, and policy enforcement actions, enhancing the overall visibility and correlation of security events.
Vulnerability Management
Vulnerability management solutions identify and prioritize vulnerabilities across an organization's IT infrastructure. By integrating with a NAC solution, vulnerability data can be used to inform access control decisions. For example, if a vulnerability management solution identifies a critical vulnerability on a device, the NAC solution can restrict or deny network access to that device until the vulnerability is remediated.
Identity and Access Management (IAM)
IAM solutions manage and enforce user identities and access privileges within an organization. By integrating with an IAM solution, the NAC solution can leverage user authentication and authorization data to enforce access control policies based on user roles, permissions, and security requirements.
Patch Management
Patch management solutions ensure that systems and applications are up-to-date with the latest security patches and updates. By integrating with a NAC solution, patch management data can be used to assess the compliance of devices and enforce access control policies based on their patch levels.
This integration creates a proactive and responsive security posture, allowing organizations to stay ahead of evolving cyber threats and maintain a secure network environment.
Advanced Features and Capabilities of NAC
How NAC Ensures Compliance and Enhances Security
Network Admission Control (NAC) solutions play a pivotal role in ensuring compliance with organizational security policies and industry regulations, while simultaneously enhancing the overall security posture of an enterprise network. Here's how NAC achieves these objectives:
Enforcing Security Policies: NAC solutions enable organizations to define and enforce granular security policies that govern network access. These policies can be based on various criteria, such as device type, operating system, software configuration, security posture, and user roles. By ensuring that only compliant devices are granted network access, NAC helps maintain a secure and controlled network environment.
Continuous Monitoring and Remediation: NAC solutions continuously monitor connected devices for changes in their security posture or compliance status. If a device falls out of compliance due to missed updates, configuration changes, or other factors, NAC can automatically initiate remediation actions, such as quarantining the device, triggering software updates, or adjusting security settings, to bring the device back into compliance.
Regulatory Compliance: Many industries, such as healthcare, finance, and government, are subject to stringent regulations and standards related to data security and privacy. NAC solutions help organizations comply with these regulations by ensuring that only authorized and compliant devices can access sensitive data and systems, reducing the risk of data breaches and potential regulatory fines or penalties.
Network Segmentation and Access Control: NAC solutions enable organizations to segment their network based on security requirements, user roles, or device types. This segmentation allows for granular access control, limiting the potential attack surface and minimizing the lateral movement of threats within the network. By restricting device communication and access to authorized resources only, NAC enhances the overall security posture of the network.
Audit Trails and Reporting: NAC solutions maintain detailed audit trails and provide comprehensive reporting capabilities, enabling organizations to demonstrate compliance with security policies and regulatory requirements. These audit trails and reports can be invaluable in the event of security incidents, enabling organizations to investigate and respond effectively while meeting any necessary reporting obligations.
By leveraging these advanced capabilities, NAC solutions ensure that organizations maintain a secure and compliant network environment, mitigating the risks associated with non-compliant devices, unauthorized access, and potential security breaches.
If you already have NAC in place, here's another blog that might assist you in mastering it.
Advanced NAC Features: Segmentation, Policies, and Enforcement
NAC solutions offer a range of advanced features that provide organizations with granular control over network access, enabling them to enforce strict security policies and maintain a secure network environment. Let's explore some of these advanced features:
Network Segmentation: NAC solutions allow organizations to segment their network into multiple logical zones or virtual local area networks (VLANs). This segmentation enables organizations to isolate different types of devices, user groups, or resources based on their security requirements and access levels. For example, guest devices can be placed in a separate VLAN with limited access, while critical systems and sensitive data can reside in a highly secured VLAN.
Granular Policy Management: NAC solutions offer advanced policy management capabilities that allow organizations to define and enforce granular access control policies based on a wide range of criteria. These criteria can include device type, operating system, user role, location, security posture, and more. Policies can be tailored to specific scenarios, enabling organizations to strike the right balance between security and usability.
Role-Based Access Control (RBAC): NAC solutions often incorporate RBAC capabilities, allowing organizations to define and enforce access privileges based on user roles within the organization. This feature ensures that users and devices are granted access only to the resources and network segments they require to perform their specific job functions, adhering to the principle of least privilege.
Guest Access Management: Many NAC solutions include features for managing guest access to the network. These features enable organizations to define specific policies and access levels for guest devices, ensuring that guest users can connect to the network in a controlled and secure manner, without compromising the security of the internal network.
Automated Remediation and Self-Healing: Advanced NAC solutions offer automated remediation and self-healing capabilities. When a device falls out of compliance or exhibits suspicious behavior, the NAC solution can automatically initiate remediation actions, such as quarantining the device, updating software, or adjusting security configurations, without requiring manual intervention.
Integration with Other Security Solutions: NAC solutions often integrate with other security technologies, such as intrusion prevention systems (IPS), endpoint detection and response (EDR) solutions, and security information and event management (SIEM) systems. This integration enables a cohesive and layered security approach, allowing for better threat detection, incident response, and access control enforcement.
Reporting and Analytics: NAC solutions provide comprehensive reporting and analytics capabilities, enabling organizations to gain insights into network access patterns, compliance trends, and potential security risks. These insights can inform decision-making processes and drive continuous improvement in security strategies.
By leveraging these advanced features, organizations can implement a robust and flexible NAC solution that aligns with their specific security requirements, enabling them to maintain a secure network environment while supporting business operations and productivity.
How Arche AI Can Help
Implementing a Network Admission Control (NAC) solution requires careful planning and consideration. But we understand the complexities involved in integrating NAC with existing network infrastructure and ensuring seamless operation with other security measures.
Our team of skilled professionals has extensive experience in deploying and configuring NAC solutions from leading vendors. We will work closely with you to evaluate your organization's requirements, network architecture, and compliance needs, ensuring that the chosen NAC solution aligns perfectly with your business objectives.
Arche's expertise goes beyond implementation. We provide comprehensive support throughout the entire lifecycle of your NAC deployment, from initial planning and integration to ongoing maintenance and optimization. Our team will ensure that your NAC solution is configured to deliver maximum security and compliance while minimizing disruptions to your operations.
Don't compromise on network security. Contact us today to schedule a consultation and take the first step towards a secure and compliant network environment.
Written by
Lakshmeesha P Kadasur
Chief Delivery Officer
Lakki, a global modernizer for 28 years, propels digital migrations. As an automation ace and revered infrastructure sensei, he spearheads our managed services ascent, optimizing, innovating, and bending space-time with cloud initiatives. Lakki's collaborative leadership manifests new realities, guiding executives beyond virtualized mobility and mainframe milestones. With allegiances to revolutionaries like IBM, Wipro, and CTS, his transitional vision elevates companies worldwide.
BLOGS
Data Center


Mastering Data Center Management with Expert Consulting
Aug 14, 2024
—
13 min read
Data Center


Engaging with Data Center Consultants for Optimal Solutions
Aug 14, 2024
—
12 min read
Data Center


Introduction to Data Center Certifications: An Overview
Aug 14, 2024
—
14 min read
Data Center


Mastering Data Center Operations with Advanced Certifications
Aug 14, 2024
—
12 min read
Ready to take your company to the next level?
Transformation starts here, talk to our experts

© Copyright 2024 Arche AI Pvt. Ltd.
Ready to take your company to the next level?
Transformation starts here, talk to our experts

© Copyright 2024 Arche AI Pvt. Ltd.
Ready to take your company to the next level?
Transformation starts here, talk to our experts

© Copyright 2024 Arche AI Pvt. Ltd.
Ready to take your company to the next level?
Transformation starts here, talk to our experts

© Copyright 2024 Arche AI Pvt. Ltd.
BLOG
Planning and Implementing Network Admission Control in Your Enterprise
BY
Lakshmeesha P Kadasur
—
14
min read


Network Admission Control (NAC) is a gatekeeper for your organization, meticulously evaluating devices before granting them network access. But implementing NAC effectively requires a well-planned strategy that aligns with your organization's unique requirements and infrastructure.
For example, a healthcare provider faces the threat of a ransomware attack due to non-compliant devices accessing the network. With a robust NAC solution in place, you can avoid such threats by ensuring that only authorized and properly configured devices gain access.
At Arche, with over 17 years of expertise in managing complex infrastructures, we understand the intricacies of deploying NAC solutions seamlessly. Our seasoned specialists have partnered with esteemed clients like Bangalore Airport, Mumbai Airport, and Sundaram Clayton, delivering innovative solutions tailored to their unique needs.
A well-defined roadmap is essential for you to implement NAC. Start by conducting a comprehensive assessment of your existing network infrastructure, identifying compatibility requirements, and defining your organization's security policies and access control objectives.
This groundwork will guide the selection and configuration of the NAC solution, ensuring seamless integration with your existing security measures, such as intrusion prevention systems (IPS), endpoint detection and response (EDR) solutions, and identity and access management (IAM) systems.
A phased rollout approach, coupled with rigorous testing and user education, can further ensure a smooth transition and maximize the benefits of your NAC investment. Continuous monitoring and timely updates are paramount, as the threat landscape is ever-evolving, and your security posture must adapt accordingly.
Are you ready to fortify your network defenses and maintain a secure, compliant environment? Book a consultation call with us today, and let's explore how our NAC expertise can become the cornerstone of your organization's comprehensive security strategy.
Deployment Strategies for NAC
How to Deploy a NAC Solution Effectively
Deploying a network admission control (NAC) solution effectively is crucial for ensuring its successful implementation and maximizing its benefits. Here's a step-by-step approach to deploying a NAC solution:
Define Policies and Requirements: Start by clearly defining your organization's security policies and requirements. Identify the types of devices that need to be monitored, the security posture criteria they must meet, and the level of access they should be granted based on their compliance status.
Conduct a Network Assessment: Perform a comprehensive assessment of your existing network infrastructure, including switches, routers, wireless access points, and other network components. This assessment will help you determine the compatibility and integration requirements for the NAC solution.
Select and Deploy the NAC Solution: Choose a NAC solution that aligns with your organization's requirements and integrates seamlessly with your existing infrastructure. Ensure that the solution supports your desired deployment model (e.g., on-premises, cloud-based, or hybrid).
Configure and Test the NAC Solution: Configure the NAC solution according to your defined policies and requirements. Thoroughly test the solution in a controlled environment to ensure proper functionality and identify any potential issues or compatibility conflicts.
Deploy NAC Agents: Install NAC agents or clients on all devices that need to connect to the network. These agents play a crucial role in assessing the security posture of devices and enforcing access control policies.
Integrate with Existing Security Solutions: Integrate the NAC solution with your existing security solutions, such as firewalls, intrusion prevention systems (IPS), and endpoint detection and response (EDR) tools. This integration ensures a cohesive security architecture and enables seamless communication and policy enforcement.
Roll Out in Phases: Rather than a big-bang deployment, consider a phased rollout approach. Start with a pilot deployment in a controlled environment or a specific department, evaluate the results, and make necessary adjustments before expanding the deployment to the entire organization.
Continuously Monitor and Update: NAC is not a one-time deployment; it requires continuous monitoring and updates. Regularly review and update your security policies, monitor the effectiveness of the NAC solution, and address any emerging threats or vulnerabilities.
User Education and Training: Educate and train your users on the importance of NAC and the procedures they need to follow to ensure compliance. Provide clear guidelines and instructions for installing and using NAC agents, as well as the consequences of non-compliance.

By following these steps and best practices, organizations can effectively deploy a NAC solution that enhances network security, ensures compliance, and minimizes the risk of cyber threats.
Key Considerations When Choosing a NAC Solution
Selecting the right network admission control (NAC) solution is crucial for ensuring its effectiveness and seamless integration with your existing infrastructure. Here are some key considerations to keep in mind when choosing a NAC solution:
Scalability and Performance
Evaluate the scalability and performance capabilities of the NAC solution to ensure it can handle your organization's current and future needs. Consider factors such as the number of devices, network traffic, and potential growth.
Deployment Model
Determine the deployment model that best fits your organization's requirements and infrastructure. Options include on-premises, cloud-based, or hybrid deployments. Each model has its own advantages and trade-offs in terms of control, flexibility, and cost.
Integration Capabilities
Assess the NAC solution's ability to integrate with your existing network infrastructure, including switches, routers, wireless access points, and other security solutions. Seamless integration is essential for effective policy enforcement and a cohesive security architecture.
Policy Management and Customization
Evaluate the flexibility and granularity of the NAC solution's policy management capabilities. Look for solutions that allow you to define and customize policies based on various criteria, such as user roles, device types, and security posture.
Supported Platforms and Devices
Ensure that the NAC solution supports a wide range of platforms and devices, including desktops, laptops, mobile devices, IoT devices, and various operating systems (e.g., Windows, macOS, Linux).
Remediation and Self-Healing Capabilities
Consider NAC solutions that offer automated remediation and self-healing capabilities. These features can help bring non-compliant devices back into compliance, minimizing the need for manual intervention and ensuring a more secure network environment.
Reporting and Analytics
Look for NAC solutions that provide comprehensive reporting and analytics capabilities. These features can provide valuable insights into network usage, security posture, and compliance trends, enabling data-driven decision-making and continuous improvement.

Vendor Support and Training
Evaluate the vendor's support offerings, including technical support, documentation, and training resources. Adequate support and training can help ensure a smooth deployment and ongoing maintenance of the NAC solution.
Compliance and Regulatory Requirements
If your organization operates in a regulated industry, ensure that the NAC solution complies with relevant industry standards and regulations, such as HIPAA, PCI-DSS, or GDPR.
By carefully considering these factors and aligning the NAC solution with your organization's specific requirements, you can make an informed decision and implement a solution that effectively enhances network security and ensures compliance.
If you're new to NAC and want to know everything about it, here's a blog that'll help.
Integrating NAC with Existing Network Infrastructure
NAC and Enterprise Network: Ensuring Seamless Integration
Integrating a network admission control (NAC) solution with an existing enterprise network infrastructure is a critical step in ensuring its effectiveness and maximizing its benefits. Seamless integration is essential for enabling efficient communication, policy enforcement, and a cohesive security architecture. Here are some key considerations for ensuring seamless integration:
Network Infrastructure Assessment: Conduct a thorough assessment of your existing network infrastructure, including switches, routers, wireless access points, and other network components. Identify the supported protocols, configurations, and integration requirements for the NAC solution.
Network Segmentation and VLAN Configuration: NAC solutions often leverage network segmentation and virtual local area networks (VLANs) to isolate non-compliant devices or enforce granular access controls. Ensure that your network infrastructure supports these capabilities and configure them accordingly.
Authentication and Authorization Mechanisms: Integrate the NAC solution with your existing authentication and authorization mechanisms, such as Active Directory, RADIUS servers, or other identity management solutions. This integration ensures that access control policies are enforced based on user identities and roles.
Network Access Devices Integration: Configure network access devices, such as switches and wireless access points, to communicate with the NAC solution and enforce access control decisions. This integration may involve enabling specific protocols (e.g., 802.1X, RADIUS) and configuring the appropriate settings.
Network Monitoring and Visibility: Incorporate the NAC solution into your network monitoring and visibility tools to ensure comprehensive visibility into network traffic, device connections, and potential security incidents.
Change Management and Testing: Implement a robust change management process and thoroughly test the integration between the NAC solution and your existing infrastructure. Conduct tests in a controlled environment to identify and address any potential issues or conflicts before deploying the solution in a production environment.
Documentation and Training: Document the integration process, configurations, and any necessary adjustments to existing network policies or procedures. Provide comprehensive training to network administrators and support staff to ensure they are proficient in managing and maintaining the integrated NAC solution.
By ensuring seamless integration between the NAC solution and your existing enterprise network infrastructure, you can maintain a cohesive and secure network environment, enforce access control policies consistently, and maximize the benefits of your NAC investment.
How NAC Works with Other Security Measures (IPS, EDR, etc.)
NAC is an essential component of a comprehensive security strategy, but it is most effective when integrated with other security measures, such as intrusion prevention systems (IPS), endpoint detection and response (EDR) solutions, and other security technologies.
This integration ensures a layered and cohesive security approach, enabling organizations to detect and respond to threats more effectively.
Intrusion Prevention Systems (IPS)
IPS solutions monitor network traffic and system activities for known threats and suspicious behavior. By integrating with an IPS, the NAC solution can leverage the IPS's threat intelligence and take appropriate actions based on detected threats. For example, if the IPS detects a compromised device attempting to connect to the network, it can alert the NAC solution, which can then deny or quarantine the device until the threat is mitigated.
Endpoint Detection and Response (EDR)
EDR solutions provide continuous monitoring and analysis of endpoint activities, enabling the detection and response to advanced threats and malicious behavior. When integrated with a NAC solution, the EDR can provide valuable insights into the security posture of endpoints, informing the NAC's access control decisions. For instance, if the EDR detects a non-compliant or compromised device, it can notify the NAC solution to restrict or block the device's network access.
Security Information and Event Management (SIEM)
SIEM solutions collect and analyze security-related data from various sources, enabling centralized monitoring, threat detection, and incident response. By integrating with a SIEM, the NAC solution can contribute valuable information about device connections, access attempts, and policy enforcement actions, enhancing the overall visibility and correlation of security events.
Vulnerability Management
Vulnerability management solutions identify and prioritize vulnerabilities across an organization's IT infrastructure. By integrating with a NAC solution, vulnerability data can be used to inform access control decisions. For example, if a vulnerability management solution identifies a critical vulnerability on a device, the NAC solution can restrict or deny network access to that device until the vulnerability is remediated.
Identity and Access Management (IAM)
IAM solutions manage and enforce user identities and access privileges within an organization. By integrating with an IAM solution, the NAC solution can leverage user authentication and authorization data to enforce access control policies based on user roles, permissions, and security requirements.
Patch Management
Patch management solutions ensure that systems and applications are up-to-date with the latest security patches and updates. By integrating with a NAC solution, patch management data can be used to assess the compliance of devices and enforce access control policies based on their patch levels.
This integration creates a proactive and responsive security posture, allowing organizations to stay ahead of evolving cyber threats and maintain a secure network environment.
Advanced Features and Capabilities of NAC
How NAC Ensures Compliance and Enhances Security
Network Admission Control (NAC) solutions play a pivotal role in ensuring compliance with organizational security policies and industry regulations, while simultaneously enhancing the overall security posture of an enterprise network. Here's how NAC achieves these objectives:
Enforcing Security Policies: NAC solutions enable organizations to define and enforce granular security policies that govern network access. These policies can be based on various criteria, such as device type, operating system, software configuration, security posture, and user roles. By ensuring that only compliant devices are granted network access, NAC helps maintain a secure and controlled network environment.
Continuous Monitoring and Remediation: NAC solutions continuously monitor connected devices for changes in their security posture or compliance status. If a device falls out of compliance due to missed updates, configuration changes, or other factors, NAC can automatically initiate remediation actions, such as quarantining the device, triggering software updates, or adjusting security settings, to bring the device back into compliance.
Regulatory Compliance: Many industries, such as healthcare, finance, and government, are subject to stringent regulations and standards related to data security and privacy. NAC solutions help organizations comply with these regulations by ensuring that only authorized and compliant devices can access sensitive data and systems, reducing the risk of data breaches and potential regulatory fines or penalties.
Network Segmentation and Access Control: NAC solutions enable organizations to segment their network based on security requirements, user roles, or device types. This segmentation allows for granular access control, limiting the potential attack surface and minimizing the lateral movement of threats within the network. By restricting device communication and access to authorized resources only, NAC enhances the overall security posture of the network.
Audit Trails and Reporting: NAC solutions maintain detailed audit trails and provide comprehensive reporting capabilities, enabling organizations to demonstrate compliance with security policies and regulatory requirements. These audit trails and reports can be invaluable in the event of security incidents, enabling organizations to investigate and respond effectively while meeting any necessary reporting obligations.
By leveraging these advanced capabilities, NAC solutions ensure that organizations maintain a secure and compliant network environment, mitigating the risks associated with non-compliant devices, unauthorized access, and potential security breaches.

If you already have NAC in place, here's another blog that might assist you in mastering it.
Advanced NAC Features: Segmentation, Policies, and Enforcement
NAC solutions offer a range of advanced features that provide organizations with granular control over network access, enabling them to enforce strict security policies and maintain a secure network environment. Let's explore some of these advanced features:
Network Segmentation: NAC solutions allow organizations to segment their network into multiple logical zones or virtual local area networks (VLANs). This segmentation enables organizations to isolate different types of devices, user groups, or resources based on their security requirements and access levels. For example, guest devices can be placed in a separate VLAN with limited access, while critical systems and sensitive data can reside in a highly secured VLAN.
Granular Policy Management: NAC solutions offer advanced policy management capabilities that allow organizations to define and enforce granular access control policies based on a wide range of criteria. These criteria can include device type, operating system, user role, location, security posture, and more. Policies can be tailored to specific scenarios, enabling organizations to strike the right balance between security and usability.
Role-Based Access Control (RBAC): NAC solutions often incorporate RBAC capabilities, allowing organizations to define and enforce access privileges based on user roles within the organization. This feature ensures that users and devices are granted access only to the resources and network segments they require to perform their specific job functions, adhering to the principle of least privilege.
Guest Access Management: Many NAC solutions include features for managing guest access to the network. These features enable organizations to define specific policies and access levels for guest devices, ensuring that guest users can connect to the network in a controlled and secure manner, without compromising the security of the internal network.
Automated Remediation and Self-Healing: Advanced NAC solutions offer automated remediation and self-healing capabilities. When a device falls out of compliance or exhibits suspicious behavior, the NAC solution can automatically initiate remediation actions, such as quarantining the device, updating software, or adjusting security configurations, without requiring manual intervention.
Integration with Other Security Solutions: NAC solutions often integrate with other security technologies, such as intrusion prevention systems (IPS), endpoint detection and response (EDR) solutions, and security information and event management (SIEM) systems. This integration enables a cohesive and layered security approach, allowing for better threat detection, incident response, and access control enforcement.
Reporting and Analytics: NAC solutions provide comprehensive reporting and analytics capabilities, enabling organizations to gain insights into network access patterns, compliance trends, and potential security risks. These insights can inform decision-making processes and drive continuous improvement in security strategies.
By leveraging these advanced features, organizations can implement a robust and flexible NAC solution that aligns with their specific security requirements, enabling them to maintain a secure network environment while supporting business operations and productivity.
How Arche AI Can Help
Implementing a Network Admission Control (NAC) solution requires careful planning and consideration. But we understand the complexities involved in integrating NAC with existing network infrastructure and ensuring seamless operation with other security measures.
Our team of skilled professionals has extensive experience in deploying and configuring NAC solutions from leading vendors. We will work closely with you to evaluate your organization's requirements, network architecture, and compliance needs, ensuring that the chosen NAC solution aligns perfectly with your business objectives.
Arche's expertise goes beyond implementation. We provide comprehensive support throughout the entire lifecycle of your NAC deployment, from initial planning and integration to ongoing maintenance and optimization. Our team will ensure that your NAC solution is configured to deliver maximum security and compliance while minimizing disruptions to your operations.
Don't compromise on network security. Contact us today to schedule a consultation and take the first step towards a secure and compliant network environment.
Lakki, a global modernizer for 28 years, propels digital migrations. As an automation ace and revered infrastructure sensei, he spearheads our managed services ascent, optimizing, innovating, and bending space-time with cloud initiatives. Lakki's collaborative leadership manifests new realities, guiding executives beyond virtualized mobility and mainframe milestones. With allegiances to revolutionaries like IBM, Wipro, and CTS, his transitional vision elevates companies worldwide.
Partner with us
Unlock your business potential with our committed team driving your success.
Read these next


Data Center
Mastering Data Center Management with Expert Consulting
By leveraging the knowledge and experience of seasoned professionals, organizations can transform their data centers from cost centers into strategic assets that drive business growth.
Read now ➝


Data Center
Engaging with Data Center Consultants for Optimal Solutions
From improving energy efficiency and reducing operating costs to enhancing security and planning for future growth, the right consultant can unlock opportunities that drive business value.
Read now ➝


Data Center
Introduction to Data Center Certifications: An Overview
For both data center professionals and the facilities they manage, the lack of industry-recognized certifications can cause a chain reaction of problems. We solve the pain in this blog.
Read now ➝
Ready to take your company to the next level?
Transformation starts here, talk to our experts

© Copyright 2024 Arche AI Pvt. Ltd.
Ready to take your company to the next level?
Transformation starts here, talk to our experts

© Copyright 2024 Arche AI Pvt. Ltd.








